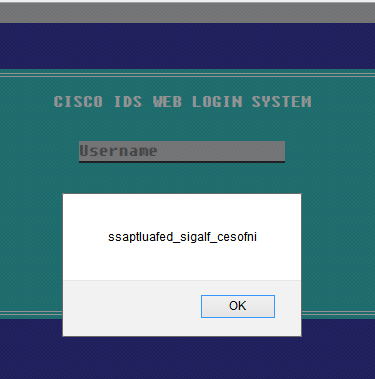
Category: Crypto
Points: 100
Description: Hint : Compatible Operation (Opération compatible)
url : http://41.231.22.133:8020/2/matrices.docx
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 0 |
| 2 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 |
| 3 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 4 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 |
| 5 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 |
| 6 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 |
| 7 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 8 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 |
| 9 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 10 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 |
DECIMAL = 64 84 76 71 48 61 70 65 82 82
ASCII = @ T L G 0 = F A R R
index = 1 2 3 4 5 6 7 8 9 10
The digit number 1 in colon index 64 is in position 7 , the index 7 in ASCII row is : F
The digit number 1 in colon index 84 is in position 3 , the index 3 in ASCII row is : L
The digit number 1 in colon index 76 is in position 8 , the index 8 in ASCII row is : A
The digit number 1 in colon index 71 is in position 4 , the index 4 in ASCII row is : G
The digit number 1 in colon index 48 is in position 6 , the index 6 in ASCII row is : =
The digit number 1 in colon index 61 is in position 10 , the index 10 in ASCII row is : R
The digit number 1 in colon index 70 is in position 5 , the index 5 in ASCII row is : 0
The digit number 1 in colon index 65 is in position 1 , the index 1 in ASCII row is : @
The digit number 1 in colon index 82 is in position 2 , the index 2 in ASCII row is : T
we get FLAG=R0@T